The server’s load is high due to a denial-of-service attack.
In DoS attacks, multiple connections are established from an IP address, and BitNinja will block the IP address if the number of connections reaches our threshold.
No software-based solution offers direct protection against DDoS attacks as all requests need to be processed in some way. True DDoS mitigation can be implemented only via some sort of hardware-based solution.
BitNinja blocks most of the infected server’s IP addresses via the challenge list or the block list, so most malicious attacks are already blocked.
Fine-tune the DoS module threshold
Changing the general threshold does not affect the ports configured individually within the module configuration file.
/etc/bitninja/DosDetection/config.ini - Lower the DoS protection threshold value in the
/etc/bitninja/DosDetection/config.inifile, thus eliminating most of the danger. - Go to
/etc/bitninja/DosDetection/config.ini - Under the [thresholds] flag, you can see the service name and the current threshold enabled.
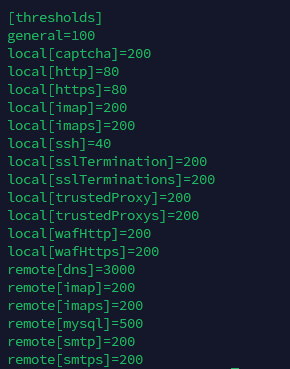
- The default threshold for ports 80 HTTP and 443 HTTPS is 80 connections per IP address. If the attack is coming via HTTP or HTTPS, then you will need to add the two lines below to the config.
local[80] = <limit here>
local[443] = <limit here> - Save your changes.
- Synchronize the configuration changes with our cloud using the command:
bitninjacli --syncconfigs - Reload the module with
bitninjacli --module=DosDetection --reloadcommand - Monitor the module logs for detected attacks:
tail -f /var/log/bitninja/mod.dos_detection.log
command:bitninjacli --module=DosDetection --show-config If the WAF module is enabled, the attackers connect via ports 60300 and 60301 due to the module redirections created on ports 80 and 443.
In these ports’ cases, the DosDetection module’s default threshold is 200.
So the below lines need to be added to the config file:local[60300] = <limit here>
local[60301] = <limit here>
Block IP manually
You can block IP addresses manually by challenge listing them or block listing them from the Dashboard.
- Go to the Firewall -> Block list menu, and add the IP addresses to your block list, or use
bitninjacli --blacklist --add=<IP address> - Insert the IP into the search field and click on the “+ challenge list” button, or use
bitninjacli --greylist --add=<IP address>
If you use a Proxy, load balancer, or CDN service, the trusted proxy module must be enabled, and the X-Forwarded-For header must be set up correctly. The instructions are here.
If the WAF module is enabled, either the Transparent proxy mode or the X-Forwarded-For header needs to be set up. The instructions are here.
