DoS vs DDoS
The server’s load is high due to (Distributed) Denial of Service attacks ((D)DoS).In the case of DoS attacks, there are multiple connections established from an IP, and BitNinja will block the IP address if the number of connections reaches our threshold.
In the case of DDoS, the attack comes from multiple IP addresses at the same time. None of the IP addresses establish enough connections at the time to identify the requests as DoS attacks but their combined number of connections still causes issues.
No software-based solution offers direct protection against DDoS attacks as all requests need to be processed in some way. True DDoS mitigation can be implemented only via some sort of hardware-based solution.
If you suspect that you are under a DDOS attack, then enable the rate limiting feature in BitNinja.
Solution
BitNinja blocks most of the infected server’s IP addresses via the challenge list or the block list. So most of the malicious attacks are already blocked
- Check the number of connections per IP addresses with this command:
netstat -ant | grep ESTAB | awk '{print $5}' | cut -d: -f1 | sort | uniq -c | sort -rn|head -n 10 - Lower the DoS protection’s threshold:
Open the Configuration menu on your BitNinja dashboard.
Select the setting level on the left side. (server-level, server group-level, account-level)
Change the value of the Threshold under the DoS Detection module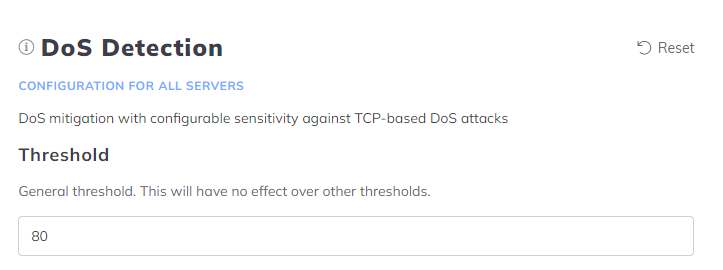
- Restart BitNinja with
service bitninja restartcommand - Run:
netstat -antu | grep -v LISTEN | awk '{print $5}' | cut -d: -f1 | sort | uniq -c again to check the results
bitninjacli --module=DosDetection --show-config command The default threshold for ports 80 and 443 is 80 connections per IP address. If the attack is coming via HTTP or HTTPS then you will need to modify the module’s config because it currently can’t be changed from the dashboard.
- Open the following config file /etc/bitninja/DosDetection/config.ini with your preferred text editor.
for example: nano /etc/bitninja/DosDetection/config.ini - Under the [tresholds] flag with the local[http] and local[https] variables you can limit the number of connections per Ip address.
By default their values are set to 200, but you can change them according to your preference.
local[http]=200
local[https]=200 - Save the changes.
- Use the command
bitninjacli --syncconfigs(Saving the changes in the file is crucial in order to synchronize the changes with our CloudConfiguration) - Restart BitNinja with the
service bitninja restartcommand.
If the WAF module is enabled then the attackers are connecting via port 60300 and port 60301.
In the case of these ports, the default threshold for the DosDetection module is also 80.
- Open the following config file /etc/bitninja/DosDetection/config.ini with your preferred text editor.
for example: nano /etc/bitninja/DosDetection/config.ini - Under the [tresholds] flag with the local[wafHttp] and local[wafHttps] variables you can limit the number of connections per Ip address.
By default their values are set to 80, but you can change them according to your preference.
local[wafHttp]=200
local[wafHttps]=200 - Save the changes.
- Use the command
bitninjacli --syncconfigs(Saving the changes in the file is crucial in order to synchronize the changes with our CloudConfiguration) - Restart BitNinja with the
service bitninja restartcommand.
You can block IP addresses manually by challenge listing them or block listing them from the Dashboard
- Go to the Firewall -> Block list menu, and add the IP addresses to your block list or use
bitninjacli --blacklist --add=<IP address> - Insert the IP into the search field and click on the “+ challenge list” button or use
bitninjacli --greylist --add=<IP address>
– If you use any Proxy or load balancer or CDN service the trusted proxy module must be enabled and the X-Forwarded-For header set up correctly. You can find the instructions here.
– If the WAF module is enabled either the Transparent proxy mode or the X-Forwarded-For header needs to be set up. You can find the instructions here.
