Proactive Malware detection:
Our Malware detection system is getting better and better. The BitNinja malware detection module, not just quarantines malware but also proactively investigates the origin of the malicious file. The Defense Robot module looks up the IP address of the uploader from the logs and also traces back the backdoors and vulnerabilities in correlation with the detected malware.
You can read more about this topic in the corresponding article.
While our database has over 20 000 Malware signatures included there might be some malware that’s signature is not yet included. That is the reason why our Defense Robot module adds malware signatures to our database. Our customers can also add malware signatures via our Malware signature system. So our Malware signature database is expanding continuously.
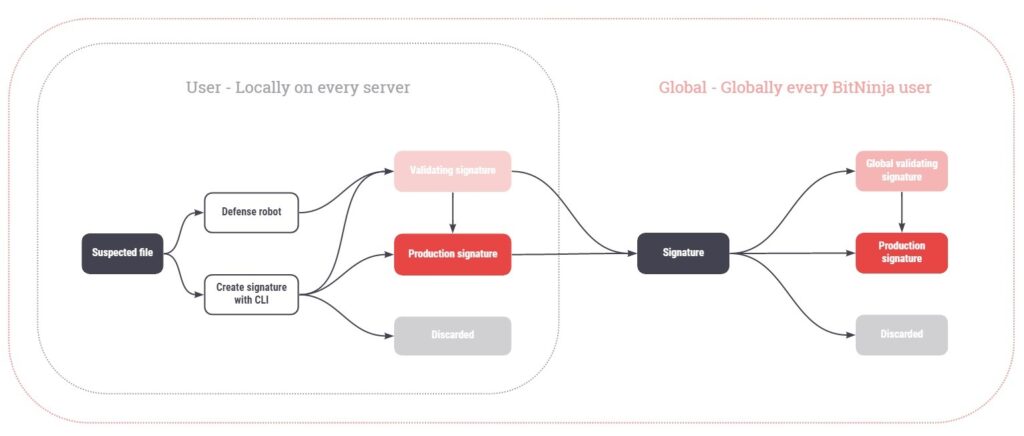
BitNinja Malware Signature system overview :
In our Malware signature system, there is a User-level and a Global level. User-level signatures take effect on all servers under our customer’s account.
On both levels, the signatures can be in three states.
- Validating: Files matching these signatures are not quarantined to avoid false positives
- Production: The matching files are quarantined
- Discarded: On user-level files with discarded signatures are restored automatically and the files will be allow listed.
If there is a malware signature in Validating or Production state it is escalated to the global level. Files matching the Global level signatures are then inspected by our tech-ninjas to make sure there are no false-positive catches in the future because of the global level signatures.
You can Check out the malware signatures from the Dashboard also. The feature is available from menu point Anti-malware under the Local malware signatures section.
Here you can filter signatures by name, signature type(structure, exact), status, and signature.
You can validate or discard the signatures using this feature.
How to handle signatures
You can use the Malware signature validating Dashboard feature for this. You can read more about this in this article.
the feature is available from the Dashboard under the Anti-Malware menu point at the Overview section.
Handle malware signatures from CLI
You can find the files matching the validating state signatures under the Anti-Malware menu point under Infected files.
These catches are highlighted and displayed as “log only”. These files are not quarantined to avoid false positives.
We recommend checking these files’ source code one by one and decide if they are malware. The signatures matching the files have an ID that is visible from the Dashboard. To see the ID you need to click on the Details button then click on Malware info.
However, it might be more useful to list them in the terminal for now as the signatures can be handled only from the terminal.
To generate a malware signature from a file you will need to issue this command: bitninjacli --module=MalwareDetection --create-signature --path=/path/to/file
For a more detailed guide about this please check out this link.
- List the signatures with this command:
bitninjacli --module=MalwareDetection --list-signatures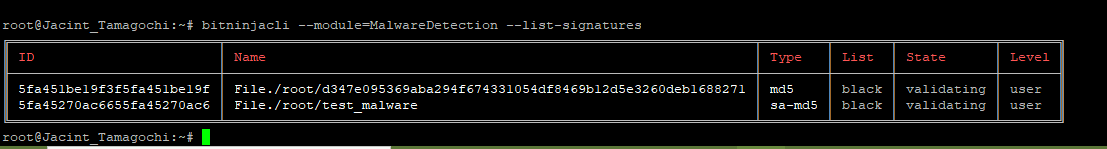
- Then inspect the file with your preferred tool.
e.g.:less test_malware - You can check how many files match the signature with this command for further investigation:
bitninjacli --module=MalwareDetection --list-signature-catches --id=<ID> - If the file is a malware issue this command including the signature’s ID.
bitninjacli –module=MalwareDetection –publish-signature –id=<ID>
e.g.:bitninjacli --module=MalwareDetection --publish-signature --id= 5fa45270ac6655fa45270ac6 - If the file is not malware you can discard the signature with this command:
bitninjacli --module=MalwareDetection --discard-signature --id=<ID>
You can contact us via chat on working days from 7:00 AM to 19:00 PM.
Or send us an email to info@bitninja.io or send a ticket from our ticketing system.
