The Defense Robot module will add malware signatures to the Malware database. The malware signatures are generated from the files that were used to upload malware. To avoid any possible issue caused by the false-positive catches, the files matching these signatures will not be quarantined. They will be logged only.
The malware signature matches are logged only because the signatures generated like this are in the “Validation” state. The signatures can be published, and this will quarantine these malware catches.
Check the malware signatures.
You can check which malware matches which signature on the Dashboard under the Infected files menu point by clicking on the Details button and then selecting the Malware Info section.
An example would be:
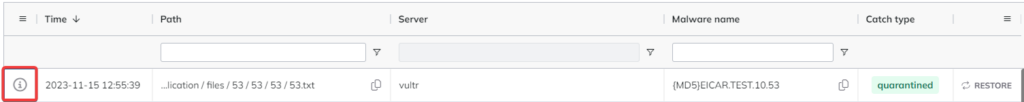
Then, you can check what other files match the malware signature with the command below.
bitninjacli --module=MalwareDetection --list-signature-catches --id=<signatureId>Quarantine the malware
The command below is setting the malware signatures’ state to “Production” from “Validating”, so the files matching these signatures will be quarantined.
bitninjacli --module=MalwareDetection --publish-signature --id=<signatureId>Discard the malware signatures
You can also discard the malware signatures in case they match non-malicious files.
The command below will remove the malware signature with the corresponding signature ID.
bitninjacli --module=MalwareDetection --discard-signature --id=<signatureId>