The WAF 2.0 module is able to block web-based attacks before they could reach the server. If a well-aimed web-based attack like a PHP code injection reaches the server it will cause serious issues on the server.
The WAF module will look like Nginx processes in the Terminal because the WAF module uses an Nginx as a reverse proxy to filter the requests.Your webserver is still up and running, of course, so the normal functionality is not affected.
Also, the most popular CMS-es and their plugins, like WordPress or Drupal have a lot of vulnerabilities that can be fixed easily with the BitNinja WAF module.
This is the only WAF module on the market that can be customized by domain patterns.
A great benefit of the domain-based rule management is that you don’t have to specify rulesets for every domain if you would like to protect a URI that is available in many domains. If you would like to get rules to every WordPress admin page on the server, you don’t have to go through every domain like domain-one.com/wp-admin/ and domain-two.com/wp-admin/ and set the same rules for them one by one.
You can get the job done by setting up the rules on a domain pattern that looks like this: */wp-admin/*
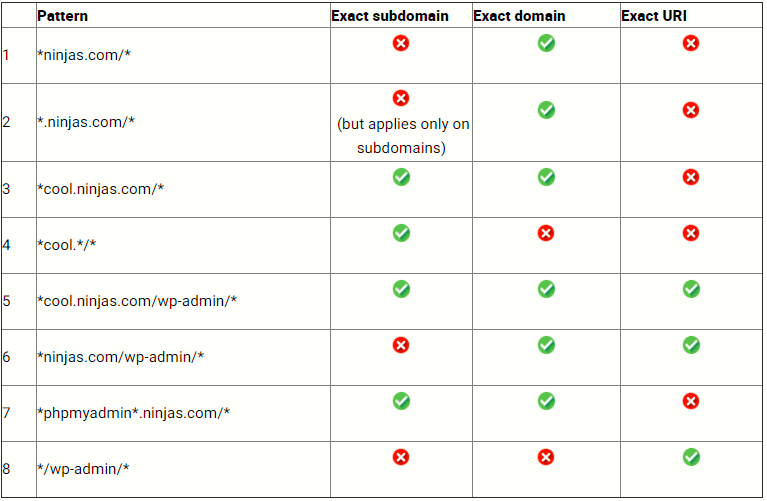
Here are some examples of the different kinds of domain patterns:
If you need more information about the module please check out these links:
https://bitninja.com/blog/waf-guide-patch-wordpress-vulnerabilities-block-web-attacks/
