If a malware’s signature is not in our malware signature database then BitNinja can not detect the malware. But you can easily add a malware signature to the database. And You can protect all of your servers instantly from that malware that has just been added as a signature.
After you have found the Malware, you can add the signature to the BitNinja malware database.
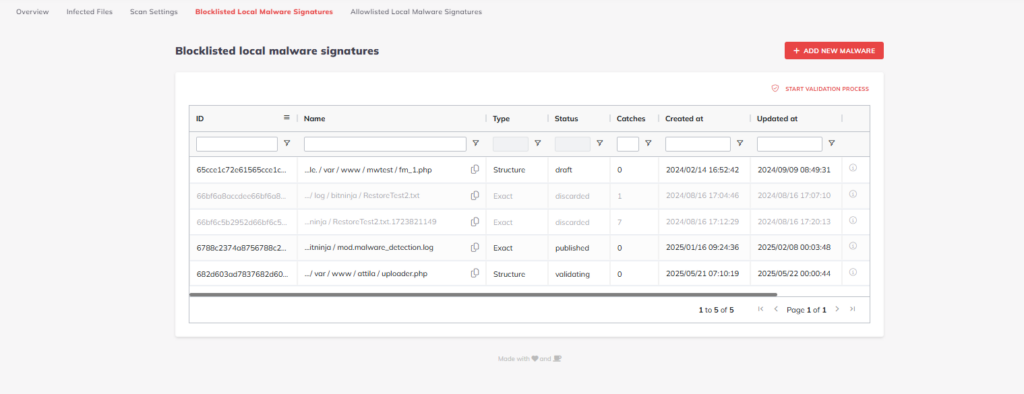
Upload malware from the Dashboard
You can also upload files from the Dashboard to generate a malware signature. You just need to click on the + Add new Malware button at the top right at the Anti-Malware / Blocklisted local malware signatures menu. The signature will be in a validating state, and the signature ID and the number of matching files on your servers will be displayed within 5 minutes in the Table of malware signatures.
They can only be added from the BitNinja CLI.
Add signature via BitNinja CLI
- Issue this command:
bitninjacli --module=MalwareDetection --create-signature --path=/path/to/file - Press p to proceed to create the signature, and then press Enter.
- Wait for the Signature to be created.
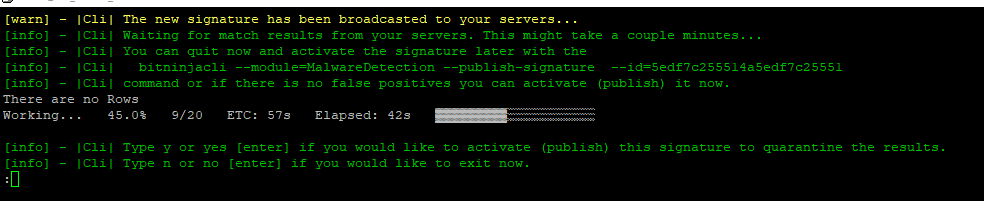
- Then press y and then enter to publish the malware signature and quarantine it on all of your servers.
bitninjacli --module=MalwareDetection --list-signature-catches --id=<signatureId> Create Snippet signature
Snippet signatures can clean files from the injected malware. At the moment snippet signatures cannot be created from the Dashboard.
At the moment the Malware detection module can detect injected codes written in PHP.
- Create a file that contains only the injected code.
- Run this command:
bitninjacli --module=malwaredetection --create-signature --path=path/to/injected/code --non-interactive --name=Name_HERE --snippet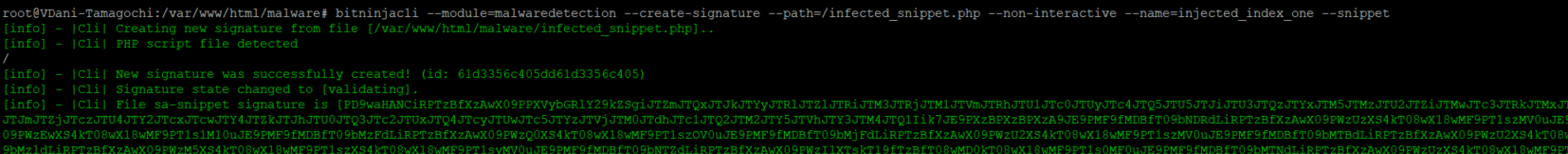
- Check if the signature is created.
bitninjacli --module=MalwareDetection --list-signatures --type=sa-snippet --state=ANY
The signature should be in validating state.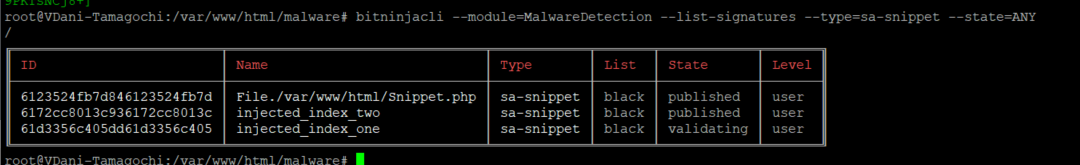
- Make sure that the signature does not cause false positives.
Check the infected files menu on your dashboard matches should be in “log only”
You can also check matches with this command:bitninjacli --module=MalwareDetection --list-signature-catches --id=<signatureID HERE> - Publish the signature:
bitninjacli --module=MalwareDetection --publish-signature --id=<signatureID HERE>
JavaScript malware signatures
An MD5 signature or a YARA rule can match JavaScript malware. As non-PHP-based malware cannot be uploaded to the BitNinja dashboard, you must create an MD5 signature using the BitNinja CLI.
We have numerous YARA rules that catch JS malware, however, we cannot automate the signature generation at the moment.
You can send Javascript malware to this email address and our malware experts.
info@bitninja.io
To make an MD5 signature for the Javascript code issue the command below: bitninjacli --module=malwaredetection --create-signature --path=path/to/JS/malware
The CLI should detect that the malware is not PHP based, and it should create an MD5 signature, so it will only match this code.
After issuing the command, you can decide to add the signature in a published state or add it in a validating (log only) state as well.
