Customer IP got blocked when he/she was editing his/her site.
This is most likely because of a false positively triggered BitNinja WAF rule. In short terms, we need to disable the rule that has been false positively triggered or allow the IP address of the customer.
Allow listing
Allow listing an IP address is a security risk because BitNinja won’t block any request from the IP address. So we recommend allow listing an IP address only if the IP address is static and you trust the IP address.
Allow listing an IP address is a security risk because BitNinja won’t block any request from the IP address. So we recommend allow listing an IP address only if the IP address is static and you trust the IP address.
Find which rule was triggered false positively.
- Enter the IP address into your search field at the top of the Dashboard.

- Scroll down and find the first incident or the incident right after the IP was delisted.
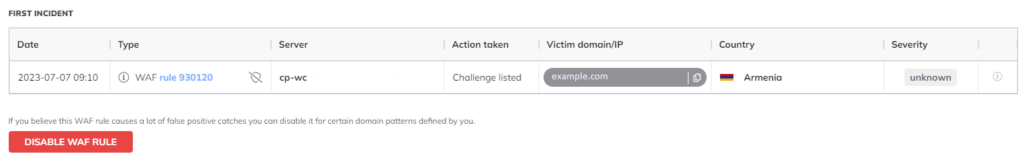
- The ID of the WAF rule that was triggered can be found in the “Type” column.
- If you think it is a false positive catch click on the “Disable WAF Rule” icon or the shield icon next to the WAF rule.
- You will see a pop window like in the picture below. In this case we have only one domain pattern, but if you have created multiple domain patterns you can select on which domain pattern you would like to disable this rule.
(You can create new domain patterns under the Firewall -> Web Application Firewall page.)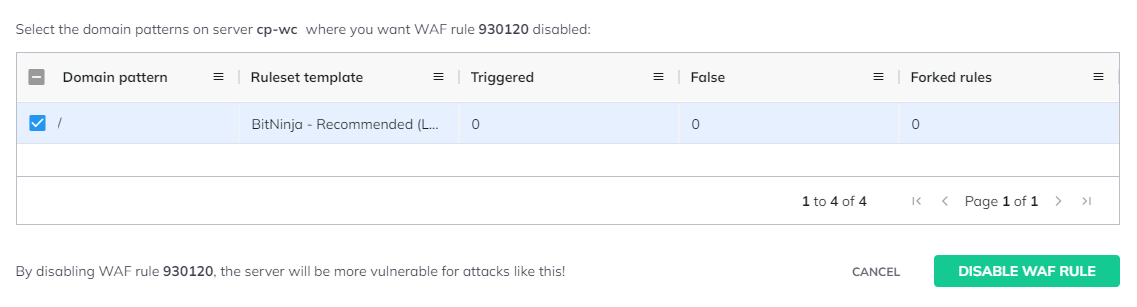
- Select the domain pattern and click the “Disable WAF Rule” button.
Allowlisting an IP address is always a security risk, as BitNinja won’t check the packages from the IP that is allowed.
Always check the request’s payload and the URL. If the payload looks suspicious and at the end of the URL there is a PHP file with 8 random characters as a name then it can be a hexa botnet attack for example.
Always check the request’s payload and the URL. If the payload looks suspicious and at the end of the URL there is a PHP file with 8 random characters as a name then it can be a hexa botnet attack for example.
